Can this work with the “off the shelf” mesh routers.
BetterNotBigger
- 2 Posts
- 23 Comments

 81·2 years ago
81·2 years agoYeah but can it host PiHole?

 11·2 years ago
11·2 years agoWe have so much computing power at home and the chances you have good reliable Internet at home are better than before. I revived 5 year old PCs and it’s way too much computing power for my self host needs. I’d have to pay $200+ a month for the same compute power in the cloud. Even a Raspberry Pi with 8GB is capable of running quite a bit for fractions of a penny in electricity.

 4·2 years ago
4·2 years agoThere’s so many services where I’m like, wow what am I even paying for? Email is one where I know exactly what I’m paying for.
Does it support syncing photos from your phone? That’s the only thing I need to get off Google Photos, I love how seamless it is.
I didn’t realize how broken SearX was until I switched to SearXNG.

 2·2 years ago
2·2 years agoDoes this game suffer from the alpha gamer?

 5·2 years ago
5·2 years agoJust… make… it… fun and I’ll play and don’t make me sign up for a service or give away my data.

 1·2 years ago
1·2 years agoLikely because the apps need access to the host and the policies were likely blocking it since it’s non-interactive.

 4·2 years ago
4·2 years ago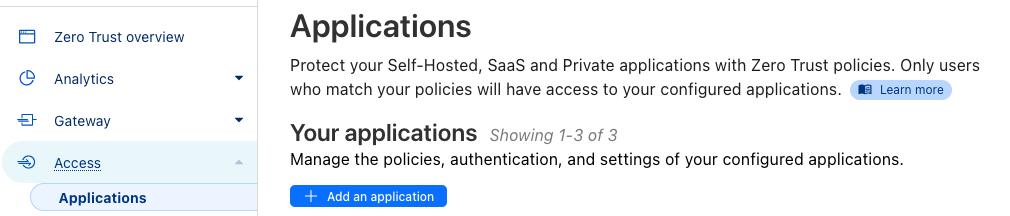
You can secure your tunnels using the Access menu and then adding an application. It should be somewhat straight-forward but you’re basically looking to create an access policy and then adding the rules you want. For example a simple one is to add an allow rule for certain emails. When you enter your email an access code will be sent to you before you can access the application resource. That’s just one of many ways to secure it using their application config and access policies.

 3·2 years ago
3·2 years agoIf you’re comfortable with using Cloudflare, you can use their zero trust tunneling and setup an application layer that adds auth to those services. I have mine protected by my GitHub login.

 1·3 years ago
1·3 years agoAre you comfortable in command line? There’s psql or there’s https://www.pgadmin.org/

 1·3 years ago
1·3 years agoHave you tried logging in with a simple postgres client?

 1·3 years ago
1·3 years agoLook under the Zero Trust category and then once there you’ll see another menu item called Access. There you’ll find Tunnels, in addition to Tunnels you can add an Application in the same Access menu to create policies that only allow certain clients to connect.

 7·3 years ago
7·3 years agoIf you only need public access to things like HTTP or SSH you don’t necessarily need to run dynamic ip and just setup Cloudflare Tunnels. So far I haven’t needed to put anything public that doesn’t run on the provided tunnels.

 1·3 years ago
1·3 years agoThis is how I got a career in Software Engineering, literally had a strong motivation to build a clan website for my Counter-Strike 1.6 crew and I just ended up learning by maintaining self-hosted websites, forums, and voip. Kept doing it over and over by building other projects and then realized people pay for this skill…

 1·3 years ago
1·3 years agoOut of all the battles for decentralization, the convenience Zero Trust provides is a trade-off I’m willing to make. I don’t see it being that much of an all-eggs-in-one-basket sort of deal since there’s no configuration done on any of my hosts. I simply install the tunnel with the token and that’s it. If there’s any reason I need to eject from Cloudflare I can simply pull the plug. Zero Trust feels more similar to relying on a nameserver with DNS management.

 1·3 years ago
1·3 years agoEmail is the only one I won’t touch, I just want it to be rock solid reliable. Unless someone can point me to a solution with fault tolerance and redundancy that’s easy to setup via Docker, I’m all ears :)

 4·3 years ago
4·3 years agoWith Cloudflare Zero Trust there is absolutely no reason for me to host on a VPS anymore. I have old hardware that’s all been revived and bootstrapped with cloudflare. If you have good Internet and decent upload IO why not start there especially if it’s just for yourself.
I’m American and I’m boycotting the hell out of it too. Supporting my neighborhood businesses.