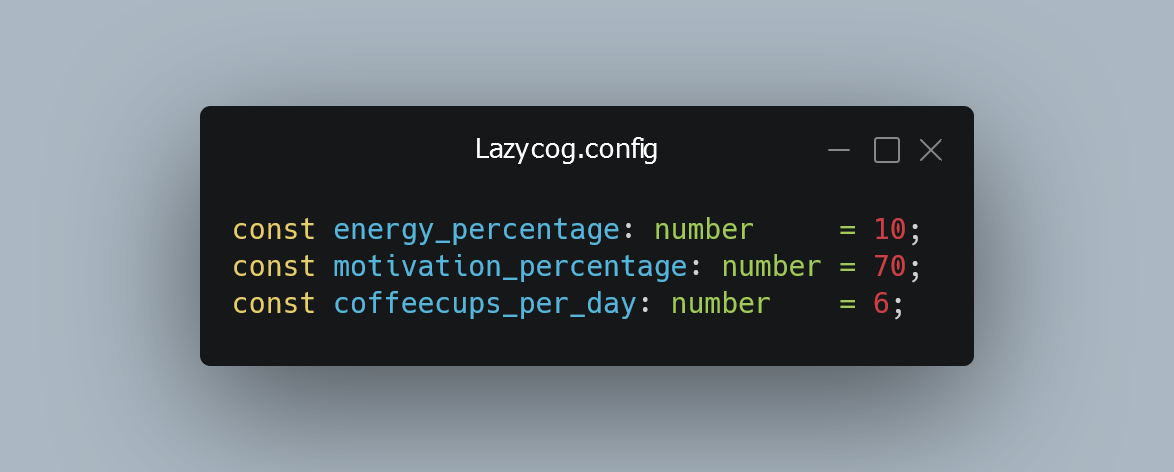
“Ah! Lore accurate John from work”
I am but a cog in a machine. A lazy one though.
- 6 Posts
- 147 Comments

 3·2 months ago
3·2 months agoDo it, 100% worth it! Also has some extra stuff for already-experienced users if it gets too easy :)

 2·2 months ago
2·2 months agoI had the same issue, this is indeed perfect for that level and a nice cozy start for your server admin journey :) I hope you enjoy it as much as I did!

 18·2 months ago
18·2 months agoI hope someone else can pitch in with a more indepth instructions, but two things I wanted to mention:
First, forget about hosting your own email from home. Seriously. Even those who do it professionally don’t want to deal with that at home. You’ll find people on fediverse who do it but I’m sure plenty will give you this same recommendation/warning. It’s a huge hassle and it’s so easy to get your domain blocked/ending up on a blacklist and way harder to get out of it.
Second, I can personally recommend https://linuxupskillchallenge.org/ if you are really starting from scratch ( there’s a community here: [email protected] ). This is how I started and set up my own linux server and started self hosting stuff on it. It’s really basic and won’t teach you everything you need but it’s a great start for setting up your own server. You can do everything with a local server at home that you have set up.
- main
- real-main
- main-2
I want to play a game. All commit info and branch stats are hidden.

 1·3 months ago
1·3 months agoThat’s a nice tip, have to try that out. Thanks!

 4·3 months ago
4·3 months agoVinegar based cleaner for everything and you are good. Recommend a separate, dedicated mirror cleaner for mirrors though. Clean weekly to reduce the need to scrub with more powerful stuff.
I admit that I once bought a book that I then donated shortly after because it was released with a cooler cover.
Then they did it again and were it not for my sad wallet I would have done it again.
Since this piece of misinformation about the monkeys has already caused damage: the monkeys are/were not infected. The truck driver told the authorities this info (which was false)
Subscription based service, huge yearly “inflation adjustments” (chase of record profits), include ads, track the person via sensors to sell the data, offer luxury packs (just enjoyment without ads, but tracking still included, just more subtle), market it and pay influencers to spread the word and document the “enjoyment” experience, lobby for government aided yearly enjoyment experiences for plebs so they don’t revolt, go public… Stonks and not an ounce of humanity left
YUP I gave up quickly! it’s truly a CSSHell lol.

 1·5 months ago
1·5 months agoThat redirect was a bit unexpected and creepy. Didn’t know medium allows your own domains for posts.
Here’s a privacy respecting frontend for that article: https://scribe.private.coffee/@trevorwooll/safe-by-default-building-a-minimal-rootless-sandbox-on-linux-4fcc02d9bed0
Soulslike CSS game: https://csshell.com/
It’s not an actual “CSS game” but instead drives the most competent CSS person over the edge.

 121·5 months ago
121·5 months agoMoved inside Europe to another country because my partner had lived 3 years in my home country and complained about everything, so we decided it’s my turn to complain about everything. One more year to go to settle the score.
On a serious note we both love things about each others country and we are both open to live in either. Living and breathing your partner’s culture and environment they grew up in is such a great way to understand them on a deeper level. I finally understand her complaints and she understands mine!

 12·5 months ago
12·5 months agoThis is true but I just want to add that instance admins can purge the uploads/posts entirely with a button that’s right next to “delete”. I recommend keeping a local copy of media you want to keep.
Mostly the purge option is used for fucked up/illegal stuff, but can’t speak for every admin. Might be someone’s go-to button for deleting posts.

 4·6 months ago
4·6 months agoI really liked the editing. The video has a good topic and it’s well presented but damn that’s some smooth editing.

 2·6 months ago
2·6 months agoI’ll gladly help, but we consider 4 months still bit fresh - mind trying to contact the mod of that community first?
It’s just that consolidation towards a community that has more history is usually nicer than bumping into “most subscribers but no content” community for new users in my opinion. But yeah that’s my opinion and the reason why I want you to talk to the mod first if possible. But for sure we are trying to reduce the amount of communities that are not being moderated and I’ll help with that. :)

 1371·7 months ago
1371·7 months agoI… Uh… Might have been raised in a culture that is quite different from yours, but I’d say very abnormal.




[email protected] (link for threadiverse to avoid leaving your own instance)