- cross-posted to:
- [email protected]
- cross-posted to:
- [email protected]
Introduction
This vulnerability report has been generated using data aggregated on Vulnerability-Lookup, with contributions from the platform’s community.
It highlights the most frequently mentioned vulnerability for August 2025, based on sightings collected from various sources, including MISP, Exploit-DB, Bluesky, Mastodon, GitHub Gists, The Shadowserver Foundation, Nuclei, and more. For further details, please visit this page.
The Month at a Glance
August 2025 saw continued activity across a range of products and vendors, with WinRAR, Microsoft Exchange (the previous month highlighted Microsoft SharePoint), and NetScaler ADC leading the sightings. Notably, several critical vulnerabilities were actively exploited, including NetScaler ADC (CVE-2025-6543 and CVE-2025-5777) and FortiSIEM (CVE-2025-25256).
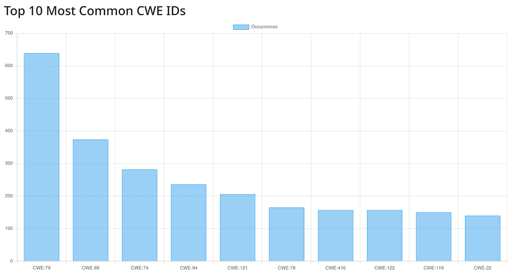
Web applications remain a frequent target, with cross-site scripting (CWE-79) and SQL injection (CWE-89) dominating the weakness landscape. The report also highlights unpublished vulnerabilities that attracted attention, suggesting ongoing targeted exploitation and zero-day activity.
Overall, the month emphasizes the importance of timely patching, monitoring for continuous exploitation, and vigilance against both well-known and emerging threats.
Top 10 vulnerabilities of the Month
| Vulnerability | Sighting Count | Vendor | Product | VLAI Severity |
|---|---|---|---|---|
| CVE-2025-8088 | 193 | win.rar GmbH | WinRAR | High (confidence: 0.9824) |
| CVE-2025-53786 | 175 | Microsoft | Microsoft Exchange Server Subscription Edition RTM | High (confidence: 0.8193) |
| CVE-2025-43300 | 128 | Apple | macOS | Medium (confidence: 0.4233) |
| CVE-2025-6543 | 111 | NetScaler | ADC | Critical (confidence: 0.9614) |
| CVE-2025-25256 | 79 | Fortinet | FortiSIEM | Critical (confidence: 0.6508) |
| CVE-2025-9074 | 65 | Docker | Docker Desktop | Critical (confidence: 0.8172) |
| CVE-2015-2051 | 62 | dlink | dir-645 | Critical (confidence: 0.54) |
| CVE-2017-18368 | 61 | zyxel | p660hn-t1a_v2 | Critical (confidence: 0.9298) |
| CVE-2025-31324 | 59 | SAP_SE | SAP NetWeaver (Visual Composer development server) | Critical (confidence: 0.9607) |
| CVE-2025-5777 | 52 | NetScaler | ADC | Critical (confidence: 0.964) |
Top 10 Weaknesses of the Month
| CWE | Count |
|---|---|
| CWE-79 | 639 |
| CWE-89 | 374 |
| CWE-74 | 282 |
| CWE-94 | 236 |
| CWE-121 | 206 |
| CWE-78 | 165 |
| CWE-416 | 157 |
| CWE-122 | 157 |
| CWE-119 | 150 |
| CWE-22 | 140 |
Most wanted vulnerabilities
Sightings detected between 2025-08-01 and 2025-08-31 that are associated with unpublished vulnerabilities.
| Vulnerability ID | Occurrences | Comment |
|---|---|---|
| CVE-2023-42344 | 8 | OpenCMS |
| CVE-2024-28080 | 4 | Gitblit |
| GHSA-42m8-jxr4-976p | 2 | Wildermyth |
| CVE-2025-9040 | 2 | Workhorse - bundle |
| CVE-2025-9037 | 2 | Workhorse - bundle |
Unpublished vulnerabilities with limited sightings:
| Vulnerability ID | Occurrences |
|---|---|
| CVE-2023-34918 | 1 |
| CVE-2025-55117 | 1 |
| CVE-2025-14553 | 1 |
| CVE-2024-55177 | 1 |
| GHSA-5pm9-r2m8-rcmj | 1 |
| GHSA-m42g-xg4c-5f3h | 1 |
| GHSA-64qc-9x89-rx5j | 1 |
| CVE-2025-7719 | 1 |
| GHSA-c2gv-xgf5-5cc2 | 1 |
| CVE-2025-55616 | 1 |
| CVE-2025-57497 | 1 |
| CVE-2025-25964 | 1 |
| CVE-2024-545078 | 1 |
| CVE-2025-25987 | 1 |
| CVE-2025-1272 | 1 |
| CVE-2025-21589 | 1 |
| CVE-2025-26517 | 1 |
| CVE-2025-9141 | 1 |
| GHSA-wrh9-463x-7wvv | 1 |
| CVE-2024-46507 | 1 |
| CVE-2025-54321 | 1 |
| CVE-2025-31143 | 1 |
| CVE-2025-31646 | 1 |
| CVE-2025-27564 | 1 |
| GHSA-r4mf-mr9h-f27m | 1 |
Continuous Exploitation
- CVE-2023-42344 - OpenCMS (also in the “Most wanted vulnerabilities” section)
- CVE-2015-2051 - D-Link DIR-645 - Sightings from MISP and Shadowserver
- CVE-2025-5777 - NetScaler ADC - Sightings from Shadowserver and many more.
Insights from Contributors
NetScaler ADC and NetScaler Gateway Security Bulletin for CVE-2025-7775, CVE-2025-7776 and CVE-2025-8424
NetScaler ADC and NetScaler Gateway Security Bulletin for CVE-2025-7775, CVE-2025-7776 and CVE-2025-8424.
Multiple vulnerabilities have been discovered in NetScaler ADC (formerly Citrix ADC) and NetScaler Gateway (formerly Citrix Gateway). Refer below for further details.
Citrix forgot to tell you CVE-2025–6543 has been used as a zero day since May 2025
Back in late June, Citrix posted a patch for CVE-2025–6543, which they described as “Memory overflow vulnerability leading to unintended control flow and Denial of Service”. Denial of service? Piff the magic dragon, who cares.
No technical details were ever published about the vulnerability. That changes today.
What they forgot to tell you: it allows remote code execution, it was used to widespread compromise Netscaler remote access systems and maintain network access even after patching, webshells have been deployed, and Citrix knew this and just didn’t mention it.
Cache Me If You Can (Sitecore Experience Platform Cache Poisoning to RCE)
The vulnerability affects Sitecore Experience Platform, a widely used Content Management System (CMS). The issue is a cache poisoning attack, which means an attacker can trick the system into storing malicious data in its cache. Later, when the system serves cached content, it unknowingly executes this malicious content.
In this specific case, the cache poisoning can escalate to remote code execution (RCE), meaning the attacker could run arbitrary code on the server, potentially taking full control of the website and the underlying system.
Thank you
Thank you to all the contributors and our diverse sources!
If you want to contribute to the next report, you can create your account.
Feedback and Support
If you have suggestions, please feel free to open a ticket on our GitHub repository. Your feedback is invaluable to us!
https://github.com/vulnerability-lookup/vulnerability-lookup/issues/